Spoofing Attacks: Everything You Need to Know

In this article
With 76 percent of this year’s cyber breaches driven by financial gain, you’d think small businesses could fly under the radar while hackers go after larger prey for bigger reward. (Remember the 2013 Target and 2014 Home Depot data breaches?) But according to Verizon’s 2018 Data Breach Report, small businesses make up 58 percent of the victims of cyber attacks. In 2016, 14 million SMBs experienced a cyber breach.
Part of what makes small businesses so susceptible is the owners’ belief that they’re the little guy and hackers will leave them alone. Makes sense, right? Unfortunately, that’s not reality. And since many don’t have the proper infrastructure or training to fight off an attack, malicious hackers can walk through the front door. Even if there are a few layers of defense, hackers can still manage to crash an SMB’s corporate networks, transfer company funds, and even get chief executives fired—all with a single email from a false source.
This is called a spoofing attack. Done right, spoofed emails can cause five- and six-figure losses for businesses. In one high-profile case, European manufacturing giant Leoni AG lost $44.6 million to email spoofers.
To mitigate these kinds of attacks, it’s important to learn what spoofing is, understand the three main types, and determine how to identify and prevent spoofing attacks from toying with your business.
What Is Spoofing?
If you look up spoofing in the dictionary, here is what you will find:
The spoofing definition does not change much when it comes to cybersecurity. Generally, in cyber terms, it is:
How does spoofing work? It’s pretty simple. Consider the practice of CEO fraud: Using email software, spoofers change the sender’s name, address, and source IP (the computer’s social security number) to make it appear as if the email is from a company’s CEO. With either an alluring or generic header, the email travels to the receiver’s inbox.
Related: What Is PKI and How Is It Implemented?
In this example, the hackers hope to trick the recipient to transfer funds or hand over sensitive information, believing they are following the CEO’s instructions. The average employee receives 121 emails each day, so spoofed email stands a decent chance of bypassing filters and going unnoticed—especially considering that 54.8 and 66.4 percent of U.S. companies have poor SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) practices, respectively.
Here’s a sample CEO fraud email:
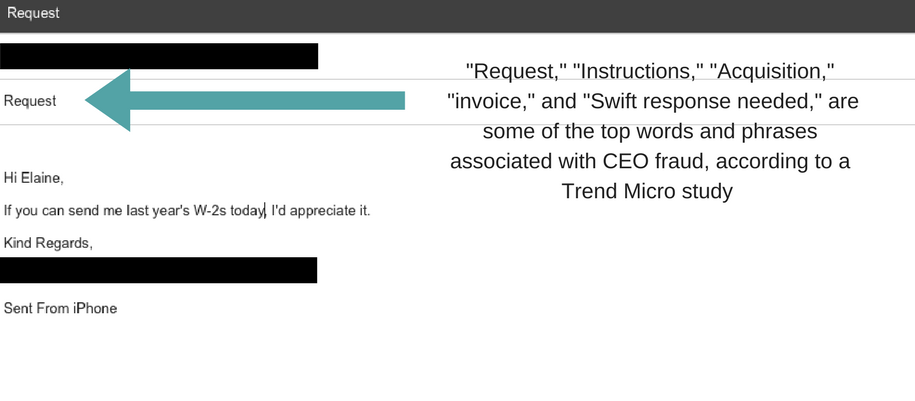
While CEO is the most frequently spoofed job position, according to a recent study, managing director comes in a not-so-close second. CFO and finance director also are among the most targeted positions.
In a high-profile case from January, the U.S. Commodity Futures Trading Commission filed anti-spoof actions against three banks and six individuals. One of the targets, well-known German banking chain Deutsche Bank, allegedly used numerous manual spoofing techniques to manipulate the prices of precious metals futures contracts.
As you can see, spoofing can be dangerous if left unchecked. Not only can it harm the economy by targeting individual SMBs, but it can influence national markets. In 2016, a London-based futures trader pleaded guilty to U.S. fraud and spoofing charges in connection with a multiple-year scheme that contributed to the 2010 “flash crash,” when the Dow Jones Industrial Average plunged 600 points in five minutes.
Of course, not all spoofing activity is rooted in the workplace. Another study revealed that more than 50 percent of open-access journals accepted a spoofed medical paper that was filled with errors.
Get To Know Other Cybersecurity Students
Dipen Patel
Cybersecurity Analyst at Accenture
Dylan Wood
Cybersecurity Career Track Student at Springboard
Rafael Ayala
Mergers And Acquisitions at Autodesk
3 Common Spoofing Methods
Below are three common types of spoofing, and tips for identifying potential attacks.
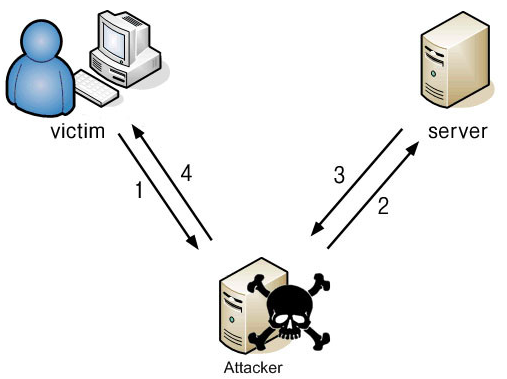
(Image source: Pentest Tips)
ARP Spoofing
Normally, your computer communicates with a wireless router on a private network: emails, searches, you name it. With address resolution protocol (ARP) spoofing, the attacker “sits” (quietly) on the network too, attempting to crack the network’s IP address.
Once in, using spoofing techniques, the hacker plays both roles: you and the router. The attacker intercepts—and yes, even modifies or stops—information to and from your computer and the router. Unless you use ARP spoofing detection software, you most likely aren’t aware that this malicious activity is happening.
To overwhelm your system and cause a shutdown, the attacker may mix up and direct several IP addresses to you. These denial-of-service (DoS) attacks can crash business’ servers and potentially suspend operations. Unfortunately, such attacks are frequent. As many as one-third of networks suffered at least one DoS attack within the last two years, according to a 2017 study.
Routinely checking your website’s stats for unexpected traffic spikes and paying attention to multiple “service unavailable” messages can help you predict possible DoS attacks.
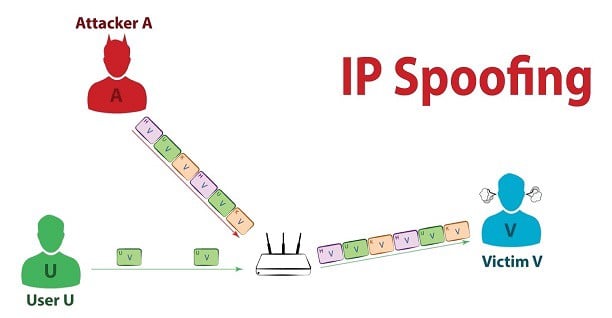
(Image source: Medium)
IP Spoofing
Considered one of the most common online sneak attacks, IP spoofing occurs when hackers impersonate an IP address for the purpose of hiding their identity and masquerading as another sender. Spoofers will send packets (data) to systems that believe the IP source is legitimate. Multiple packets flood servers, triggering crashes and successful DoS attacks.
Slow or unresponsive web pages is a common sign of a DoS attack. Backing up important data that is on the cloud is a good fail-safe strategy to prevent data loss from DoS attacks targeting cloud services, which have become more widespread since 2016.
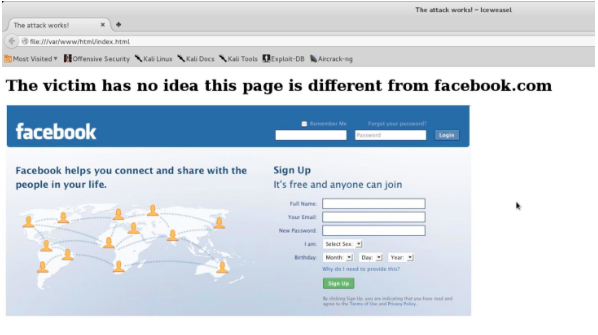
(Image source: Null Byte)
DNS Spoofing
Thanks to the DNS server, you do not have to remember Yahoo!’s or AOL’s IP addresses, much less any other domain’s. The DNS (domain name system) server is a database made up of public IP addresses and corresponding hostnames. DNS spoofing occurs when hackers mix these up. Instead of going to Google’s search page when you enter appropriate URL, hackers direct you to a spoofed domain.
Google is in the process of removing spoofed domains from its search engine, but keeping an eye out for inconsistencies and errors on sites helps to identify DNS spoofing.
How to Protect Your Business Against Spoofing
Add these fail-safe tools and cybersecurity best practices to your cyber arsenal to prevent spoofing attacks:
- Stick to two-factor authentication
- Consistently update your network and upgrade to the latest cybersecurity software
- Set up firewalls to block false IP addresses
- Use penetration testing to identify vulnerabilities in your network
- Only visit sites with proper SSL certification
- Install anti-spoofing detection software
- Avoid giving away personal information online, email included
- Do not click on unknown email links or attachments
- Provide cybersecurity training to employees to broaden knowledge and minimize insider and outsider attacks
With these prevention methods and some cyber know-how, you can mitigate spoofing attacks and keep your business, employees, and customers safe. Although there is no single-hand solution, staying up to date on the latest spamming tactics allows you to be proactive and bounce back should spoofers strike.
Related: What Does a Cybersecurity Analyst Do?
This post was written by Elizabeth Mack. Elizabeth is a Southern California-based freelance writer specializing in career and technology—specifically cybersecurity and SaaS. She’s obsessed with Thai food, loves coffee, and enjoys new perspectives.
Since you’re here…
There are hundreds of thousands of vacant cybersecurity jobs, and one of them has your name on it. You can enter the industry in 6 months flat with our Cybersecurity Course. We’ve helped over 10,000 students make huge career changes with our fully flexible mentor-led bootcamps. Explore our free cybersecurity curriculum today to start your career switch story.







